Enlarge (credit: Getty Images)
Recently detected Android malware, some spread through the Google Play Store, uses a novel way to supercharge the harvesting of login credentials from more than 100 banking and cryptocurrency applications.
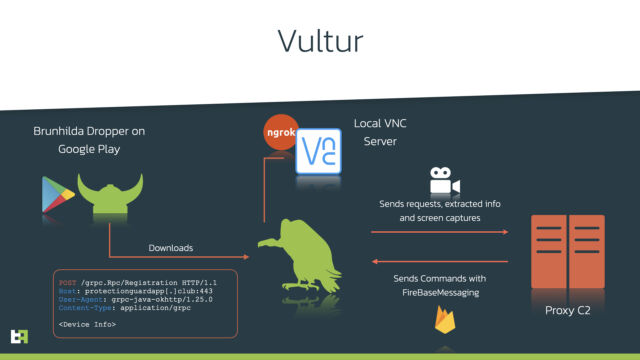
The malware, which researchers from Amsterdam-based security firm ThreatFabric are calling Vultur, is among the first Android threats to record a device screen whenever one of the targeted apps is opened. Vultur uses a real implementation of the VNC screen-sharing application to mirror the screen of the infected device to an attacker-controlled server, researchers with ThreatFabric said.
The next level
The typical modus operandi for Android-based bank-fraud malware is to superimpose a window on top of the login screen presented by a targeted app. The “overlay,” as such windows are usually called, appears identical to the user interface of the banking app, giving victims the impression they’re entering their credentials into a trusted piece of software. Attackers then harvest the credentials, enter them into the app running on a different device, and withdraw money.